Push and Pull data - Pros and Cons and When to Use Each Approach
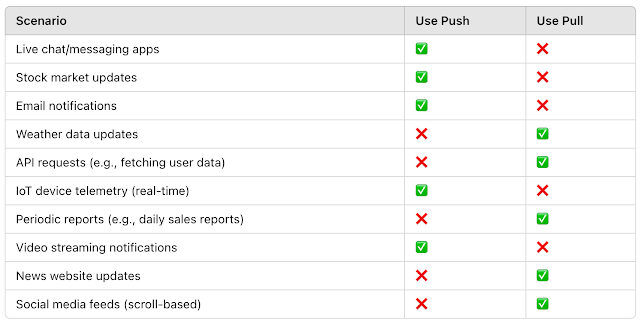
When designing data flows, choosing between pushing (sending data proactively) and pulling ( retrieving data on demand ) depends on factors like efficiency, latency, scalability and control. Pushing Data: The source system sends data automatically to the destination as they occur. Pros of Pushing Data : Lower Latency: Updates are delivered in real-time or near real-time. Efficiency for High-Frequency data: Reduces the need for repeated requests when data updates frequently. Less Client-side Processing: The destinatiuon system doesn't need to monitor or poll for changes. Reduces Server Load (for clients). Eliminates unnecessary requests when no new data is available. Cons of Pushing Data: Potential Overload: if too much data is pushed once, the receiver may struggle to process it efficiently. More Complex Error Handling: if the destination is down, data might be lost without a proper retry mechanism. Requires Efficient Event Handling: The destination must be able to hand...